

AUTONOMOUS or UNATTENDED ACCESS CONTROL
Some of our Customers want to be able monitor access and egress of Visitors without the presence of Security Staff with Scanners. This requirement can arise under many situations where Guests do not want to be scanned or the rate of visitor numbers makes attended scanning a barrier to frictionless and timely access.
Breakout sessions is one example where attendance may be mandatory but attended scanning not practical. Coupled with an NFC Chip Cashless and other services can be encorporated.
THE TECHNOLOGY
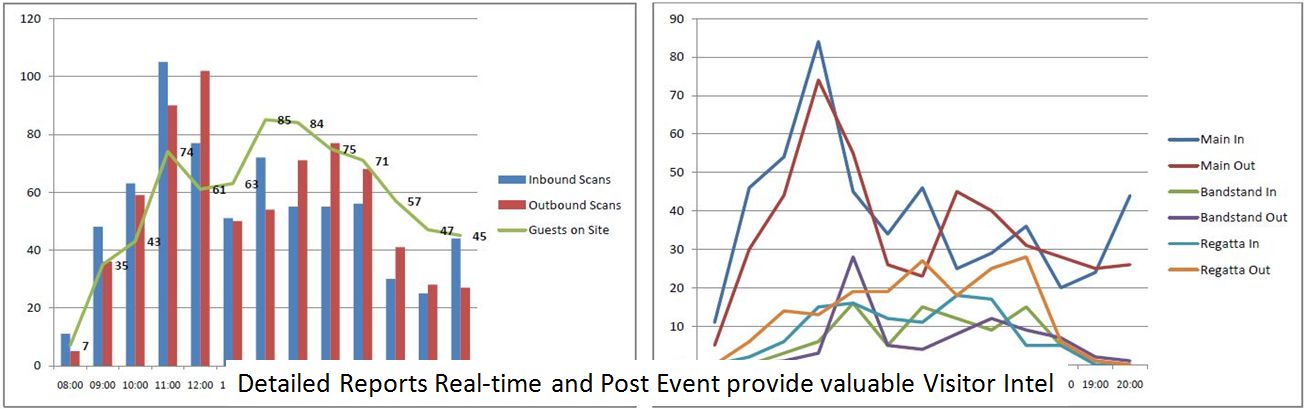
Using a type of RFID Chip that performs differently to normal NFC or HF RFID means that strategically positioned antenna (scanners) can scan individuals from a range up to four metres. The scanning antenna are constantly sending out a signal and recording all of the UHF (ultra high frequency) chips in range. The management system attached to the antenna then sorts this data to show access and egress records, time spent on site and how many times visitors return. A short video illustrates to operation and the location of the scanners.
A traffic light system can alert security when a false or void UHF Chip is detected.
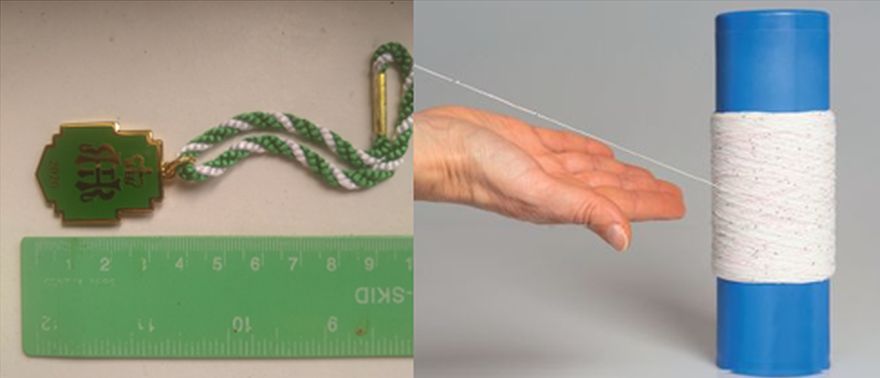
UHF CHIP
The challenge for a particular customer was how to attach a UHF Chip to a metal badge. It is not possible to attached UHF Chips on to metal, unless a bulky layer of foam is used to offset the chip from the metal. In this instance we sourced a UHF Chip embedded within a 30 cms thread which was threaded seamlessly into the cord of the lapel badge.



Make a free website with Yola